Why NEXTDATA ?

Uniqueness
The device fingerprint rematching rate is as low as one in ten thousand, ensuring a one-to-one correspondence between each device and its ID, placing it at the forefront of the industry

Multiterminal Application
Compatible with over 32,000 device models worldwide, supporting Android Q and iOS 14.5 or later versions

Abundent Labelling System
Over 40 risk labels for devices, including false device labels, machine-controlled device labels, and suspicious device labels. Additionally, there are over 50 basic attribute labels

Strong Stability
Embedded within the app, stable with zero crashes, ensuring stable data collection and accurate label precision across different vendor environments

Reliable Privacy Protection
Attaining the highest-level protection certification, Level 3, for non-banking institutions, compliant with personal data protection laws, GDPR requirements for international expansion. It ensures no privacy breaches, supports transparent audits, and allows for the customization of data collection fields
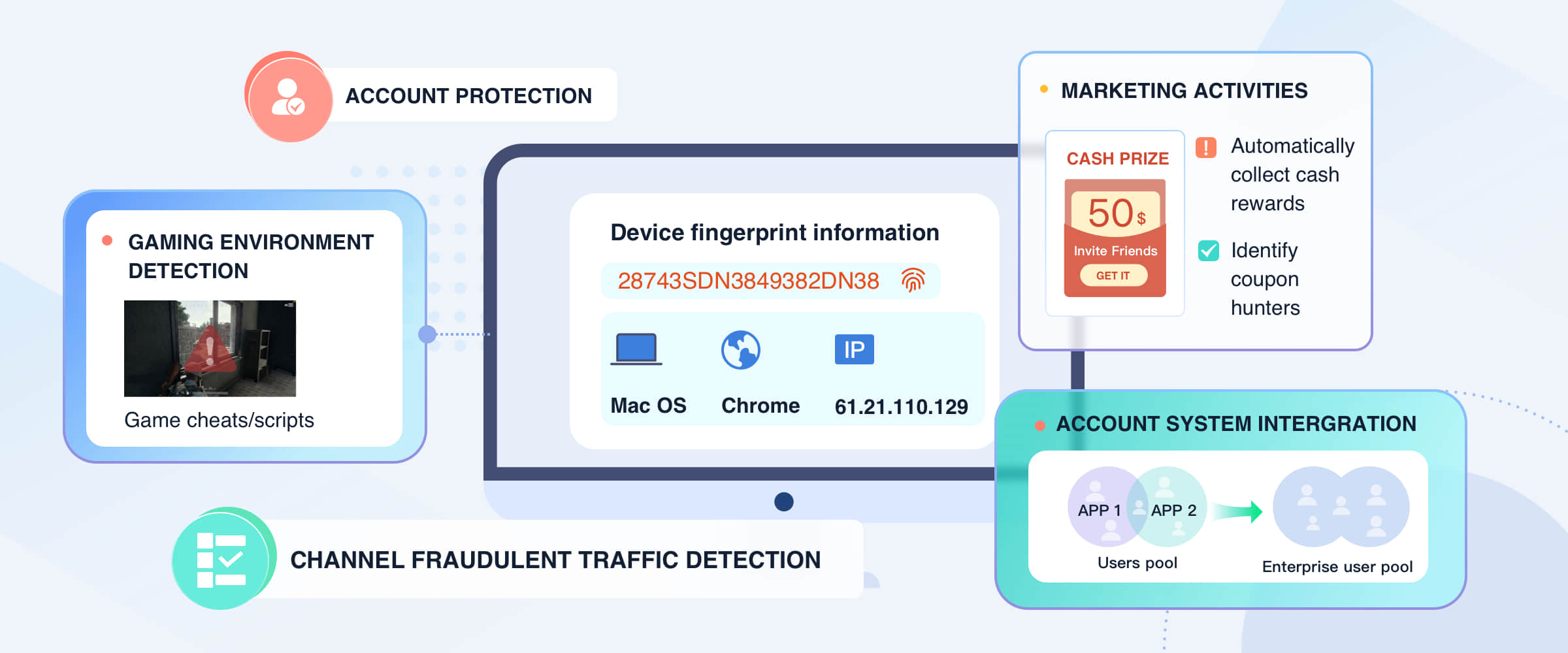
Support the Detection of Various Risky Business

Device Unique Identifier
This can support and generate a unique device identifier for every mobile device to help businesses in forming reliable user relations with advanced account security

Fake Device Label
Fake Device Label includes over ten device labels that can identify pc emulator, cloud phone device, location spoofing, multi-boxing device with operating system (multi-instance), multi-boxing device with cheating apps, altered device, farm device, offer wall(reward wall) devices
Machine-Controlled Device Labels
This label can recognize more than ten types of device risks associated with the latest black-market use of automatic control tools and script tools, including tools like device macros

Suspicious Device Labels
This label can return over twenty suspicious devices risks such as root experience, no sim card on board, VPN usage, reset device

Device Property Labels
This label return 50+ dimensions of device attribute fields, including Android ID, app version, device model, etc
Support Device Fingerprint Detection in Multiple Scenarios
Product Superiority

The product evolves rapidly, offering a global SaaS risk control network with sub-second iterations
This complete evolutionary cycle encompasses real-time awareness of black-market dynamics, pattern discovery, data characteristics, model iterations, gray-scale validation, business interception, and case-based learning. Real-time stream processing is used to achieve real-time updates of models and behavioral profiles, thus creating a sub-second iteration global SaaS risk control service network

An end-to-end, full-stack strategy system, achieving high recall and high accuracy in fraud detection
Deeply integrating models such as GCN, Node2V, Louvain, GAN, GBS, LSTM, and more to construct a full-stack model system, thereby preventing false positives and false negatives associated with a single model, and achieving high accuracy in fraud detection

A comprehensive scenario strategy system to prevent various business risks
Utilizing techniques such as group mining, correlation analysis, time-domain analysis, machine learning, deep learning, and drawing from over a decade of professional risk control and anti-fraud experience across multiple industries, we have built an extensive and complete strategy system to comprehensively identify business risks

Lightweight and straightforward integration solution, quick deployment
Utilizing industry-standard API interfaces for easy and simple integration, while also benefiting from the sub-second iterations and self-upgrading capabilities offered by the SaaS cloud service model
Quick Access Guide

One-click Application
Click free trial to create a test service
Solution Formulation
Our solutions experts will contact you promptly
API Interface
Test quickly connects to the product for product testing